S/MIME in The Bat!
The Bat! email client implements S/MIME (Secure/Multipurpose Internet Mail Extensions) protocol to for End-to-end encryption (E2EE), where only the communicating users can read the messages. It prevents potential eavesdroppers - including telecom providers, Internet providers, and even the provider of the communication service - from being able to access the cryptographic keys needed to decrypt the conversation.
The Bat! supports S/MIME in two modes: via Internal Implementation or via Microsoft CryptoAPI.
Before encrypting or signing messages with S/MIME, you need to obtain certificates of the encryption keys.
The following sections describes S/MIME in detail:
Certificate Management
Internal S/MIME Implementation
Microsoft CryptoAPI
Electronic Signature
Encrypting Messages
Decrypting Messages
S/MIME Standard
Certificate Management
Obtaining a Certificate
You can get an S/MIME certificate from a certification authority (CA) or create a self-signed certificate. Using internal S/MIME implementation you can create a certificate: access the Account -> Properties -> General menu and click the "Edit personal Certificates" button.
In the new window click the "Generate" button and edit certificate items and values. At the final stage input the passphrase to protect the certificate.
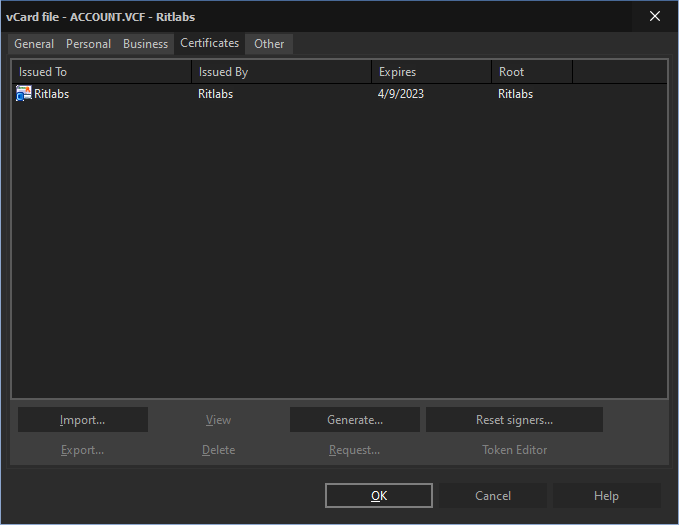
Your correspondent who received your signed message will have to add your self-signed certificate to the certificate store only once. You can also send your certificate to a CA to certify it.
It is not necessary to create a certificate in The Bat! You can get it directly from any Certification Authority. Once you get the certificate, import it to the program. You can now delete your self-signed certificate and use the CA-issued one to sign and decrypt messages.
View Certificates
To view certificates of your address book contacts, open the Address Book (F8), select a contact and access the Edit -> Properties menu. You can view the certificate under the Certificates tab.
To view your own certificate, access the Account -> Properties -> General -> Edit personal Certificates menu. Select the certificate and click "View".
In the Details section you will see the serial number of your certificate and its version, signature algorithm (calculation method used in producing a signature from this certificate), validity period, issuer and subject (name and email address associated with this certificate).
In the Certification Path section you can see all signatures associated with the certificate up to the CA.
Export Certificate
Internal implementation of S/MIME allows you to export selected certificates to a file for backup or distribution (e.g. import into other programs or The Bat! installations).
To export a certificate, access the Tools -> Address Book menu (F8), select the contact and go to its Properties (Edit -> Properties). Under the Certificates tab select the needed certificate and click "Export". Certificates are exported to known, open formats only.
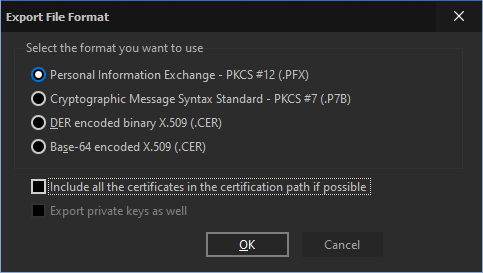
- Personal Information Exchange – PKCS #12 (.PFX). This format allows export of a group of certificates as well as their private keys, which are encrypted using the same passphrases as in The Bat!; the corresponding certificates are not encrypted. Conforms to PKCS 12 v1.0: Personal Information Exchange Syntax developed by RSA Laboratories.
- Cryptographic Message Syntax – PKCS #7 (.P7B). This format allows the export of a group of certificates to a file based on a signed message packet (the packet has no message body and no signature, only the attached certificates). It contains only certificates but no private keys. This is the most commonly accepted format. It Conforms to RFC- 2630 (Cryptographic Message Syntax).
- DER encoded binary X.509 (.CER). This format allows you to export a single certificate without associated private keys. The output file contains a single X.509 certificate encoded according to DER-encoding rules; it will not be encrypted. If a certificate contains a private key, the key may be exported to a separate binary file, unencrypted, corresponding to PKCS#1 DER-encoded RSA. Beware: not all software applications can handle DER encoded binary X.509.
- Base-64 encoded X.509 (.CER). This format is based on DER encoded binary X.509, but additionally encodes with a Base64-wrapper. The file only contains printable characters, which can easily be put into an email or on a website. Base-64 encoded X.509 is widely supported. Private keys can be exported to separate text files.
- Include all the certificates in the certification path if possible
Note: This option works with standards supporting multiple certificates in a single file.
- Export private keys as well
Import Certificate
There are several methods of importing certificates into The Bat!:
Method 1
Open the message containing a certificate and view the certificate by clicking the icon
 which you will see on the right-hand side of the headers pane. Select the certificate and click "View". In the General section click the "Add to Address Book" button to import the certificate. Next time you receive an email signed with this certificate you will see the icon
which you will see on the right-hand side of the headers pane. Select the certificate and click "View". In the General section click the "Add to Address Book" button to import the certificate. Next time you receive an email signed with this certificate you will see the icon  on the headers pane, which means that the signature is valid.
on the headers pane, which means that the signature is valid. Method 2
Access the Address Book (F8), select the contact whose certificate you want to import and double-click it to open its properties. You can also use the Edit -> Properties menu to access the Properties of a contact. Switch to Certificates tab, click the "Import" button and select the certificate.
Internal S/MIME Implementation
You can switch to internal S/MIME implementation using the Options -> S/MIME and TLS menu.
The main difference between the two engines is that internal implementation does not use any outside code. The disadvantage is the lack of flexibility: When it comes to using different third-party algorithms, storage media, or devices that perform certain operations at a hardware level, you will need to use the CryptoAPI engine, but it may work differently or with some limitations under different versions of Microsoft Windows.
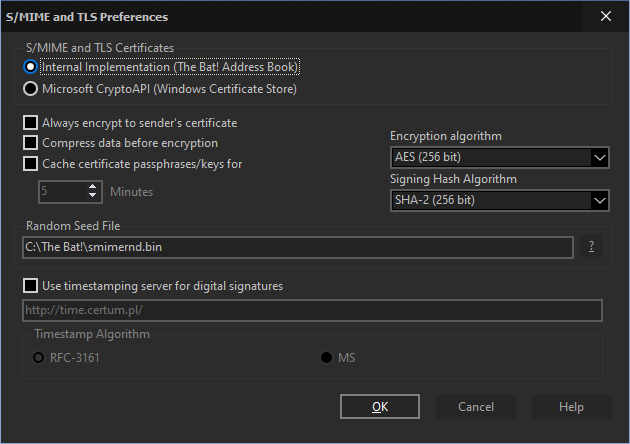
If you choose the Internal Implementation, the following options will be available:
Always encrypt to sender’s certificate
This option allows encrypting sent messages to your own certificate – In this case you will be able to decrypt sent messages.
Compress data before encryption
Compression reduces message size and increases resistance to attacks.
Beware: S/MIME compression may not be supported by other S/MIME-enabled email clients. Microsoft CryptoAPI does not support it.
Cache certificate passphrases/keys for
Choose the time interval a passphrase should be stored in memory before you have to re-enter it.
You can select the preferred "Encryption algorithm" from the dropdown menu.
Signing Hash Algorithm specifies which hash algorithm is used. The default SHA-1 is widely supported and is highly secure. If your recipient's S/MIME implementation does not support SHA-1, choose MD-5.
"Random Seed File" path specifies the location where random data for key generation is stored.
You can also enable the "Use time stamping server for digital signatures" option to add a timestamp to your signature – In this case the recipient will see the exact time the message was signed.
Microsoft CryptoAPI
This engine is part of Microsoft Windows. For further information consult Microsoft's documentation.
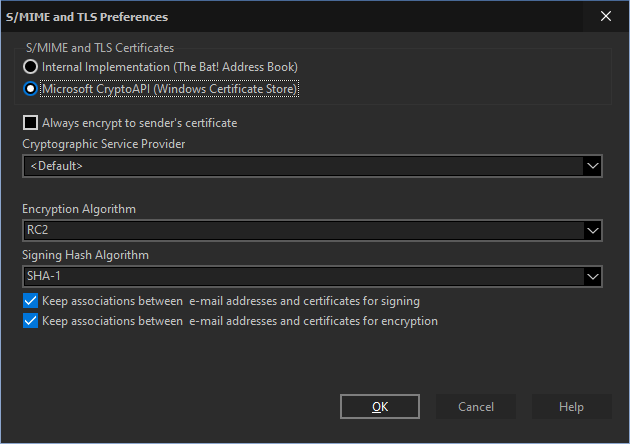
Always encrypt to sender’s certificate
This option allows encrypting sent messages to your own certificate – In this case you will be able to decrypt sent messages.
You can choose the preferred "Cryptographic Service Provider" from the dropdown menu.
Note: If you choose a provider from the list, The Bat! will use only this provider; with selected, CryptoAPI will select the required providers corresponding to a particular algorithm, key type or certificate.
Depending on the selected Cryptographic Service Provider you can choose the Encryption and Signing Hash Algorithms.
Note: The Bat! adds one signature to a message when using Microsoft CryptoAPI.
If the "Keep associations between email addresses and certificates for signing" option is active, The Bat! remembers the certificate used for signing messages.
If you enable the "Keep associations between email addresses and certificates for encryption" option, the program will remember the certificate that was used for encryption.
Electronic Signature
An electronic S/MIME signature ensures that any attempt to manipulate messages between you and the recipient can be easily detected. The Bat! will even flag compromised messages in the message list automatically.
Manually Signing Messages
Select the "Enable S/MIME" option in the Privacy menu in the Message Editor. Then enable the "Sign when Completed" option in the Privacy menu or click the icon
 on the Security toolbar.
on the Security toolbar. Automatically Signing Messages
You can set automatic signing as well: Enable the "Sign when Completed" and "Enable S/MIME" options in the Account -> Properties -> Options menu.
Tip: Use the %SIGNCOMPLETE macro in the templates to enable automatic signing of messages.
Verifying Signature
A yellow checkmark appears on the message flag if a message is signed
 . To verify signature, select the message and use the Tools -> Privacy -> Verify Signature menu (Shift+Ctrl+C) or click the icon
. To verify signature, select the message and use the Tools -> Privacy -> Verify Signature menu (Shift+Ctrl+C) or click the icon  on the right-hand side of the headers pane.
on the right-hand side of the headers pane. The Bat! verifies S/MIME signatures automatically and marks messages with either a tick
 or a cross
or a cross  to indicate whether or not the message signature is valid. These icons appear on the headers pane.
to indicate whether or not the message signature is valid. These icons appear on the headers pane. Encrypting Messages
Using encryption, you can ensure the privacy of your correspondence. Only those people to whose public key the message is encrypted to, are able to read it. To encrypt messages, you have to import the recipient’s certificate into the program.
Beware: Some governments may restrict encryption.
Manually Encrypting Messages
Select the "Enable S/MIME" option in the Privacy menu in the Message Editor. Then enable the "Encrypt when Completed" option in the Privacy menu or click the icon
 on the Security toolbar. You will be able to continue editing messages as they will be encrypted directly before you send them out.
on the Security toolbar. You will be able to continue editing messages as they will be encrypted directly before you send them out. Automatically Encrypting Messages
You can set automatic encryption as well: Enable the "Encrypt when Completed" and "Enable S/MIME" options in the Account -> Properties -> Options menu.
Tip: You can use the %ENCRYPTCOMPLETE macro in the templates – in this case messages will automatically be encrypted before sending.
Note: Remember to encrypt the message using your certificate as well, otherwise you will not be able to read encrypted sent messages.
Decrypting Messages
To decrypt a message, select it and choose the "Decrypt" option in the Tools -> Privacy menu (Shift+Ctrl+D).
The decrypted message is not stored in the message base to protect your privacy. Every time you want to read an encrypted message, you have to decrypt it again. You can decrypt and save the message if needed, by selecting the respective option in the Tools -> Privacy menu (Shift+Ctrl+G).
Note: The Bat! automatically checks signature, if there is one.
S/MIME Standard
S/MIME is a standard for signing and encrypting email. It conforms to the following RFCs:
- RFC2632 S/MIME Version 3 Certificate Handling
- RFC2633 S/MIME Version 3 Message Specification
- RFC2634 Enhanced Security Services for S/MIME